OSI Model Explained Fully With Complete Details
What is the OSI model? The model is a hypothetical heap of seven layers that can be utilized as a kind of perspective to help see how systems work.
The model was acquainted with institutionalized arrangements in a way that allowed multi-vendor structures before this.
You may, in all probability, have a one-dealer mastermind because the devices from one seller couldn’t communicate with others.
It’s important now that we don’t really utilize the OSI model we use something many refer to as the tcp/ip model the ideas are actually the equivalent the layers are marginally extraordinary so if we don’t utilize the OSI model for what reason would we try learning it well that is because despite everything it referenced a ton when investigating or portraying system tasks how about we investigate the layers beginning from the base.
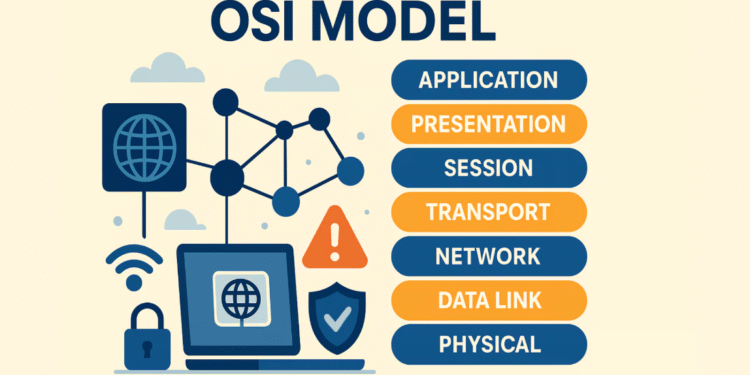
OSI MODEL LAYERS TYPE
Up layer one is the physical layer. The physical layer is the lowest layer of the OSI model it’s key obligation is to convey the information crosswise over physical Hardware.
For example, Ethernet links layer two is the information connection layer at this layer the physical delivers are added to the information this is the source and goal MAC tends to switches are situated at this layer the system layer handles IP tending to and directing at this phase of the OSI model the source and goal IP address are included reuters work this layer in this manner the vehicle.
The vehicle layer of the OSI model includes the vehicle conventions, for example, TCP and UDP. TCP, for instance, is utilized for error handling and sequencing to guarantee no information is lost.
This layer additionally includes the source and goal port numbers layer 5 session. This layer is in charge of setting up and ending associations between gadgets, layer 6 introduction.
This layer designs the information in a manner that the accepting application can comprehend. This layer is additionally ready to encode and decode information if necessary layer 7 application.
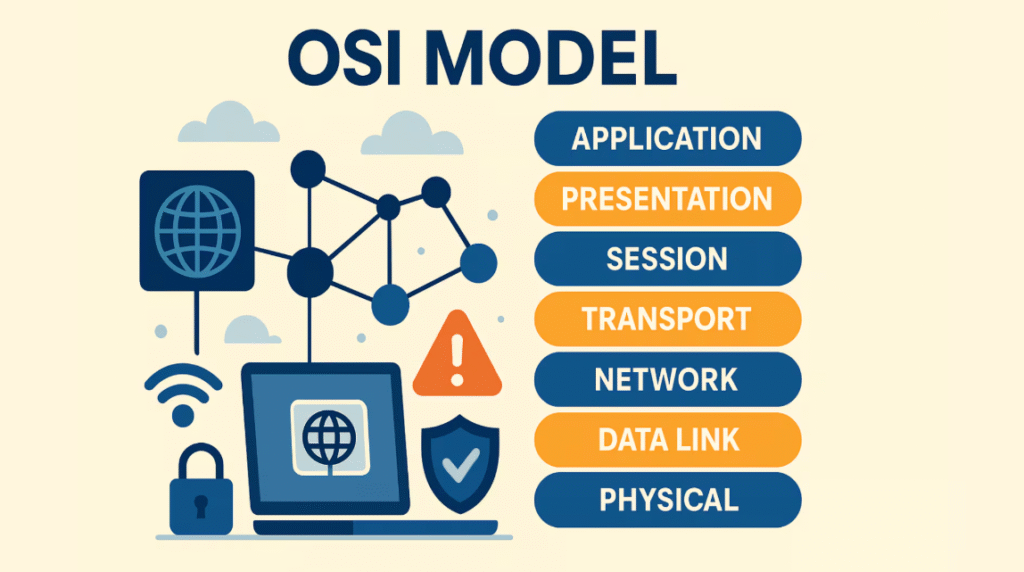
This layer is the place the application and client share application-specific conventions are utilized here.
For example, SMTP in case you’re sending an email for instance a great method to recall these layers is just all individuals appear to require information preparation a PS T and DP so to completely see how this model functions, you have to see a certifiable model.
Suppose you send an email, the information goes through the OSI model, including handling information at each layer, and this procedure is called encapsulation.
Stage one the application layer our heap makes the information the email you composed the email addresses and so on and so on and prepares to send it utilizing SMTP which is the Simple Mail Transfer Protocol stage 2 introduction there the information is organized in a manner the getting gadget will comprehend in this model most likely a SC III.
This layer could likewise scramble the information if necessary. Step 3: session layer a session with the accepting mail server is a beginning venture for the vehicle.
This is the place it chooses to utilize TCP or UDP for this situation. We’ll utilize TCP to ensure each parcel gets conveyed likewise the source and goal port is added to the information stage 5 Network.
The IP address of the mail server is included as the goal and the source IP address is additionally included through the information stage 6 information connection the MAC address of the switch and the source MAC address of the host is added to the information.
Stage 7 physical the information is conveyed on the system utilizing Ethernet so when the information arrives at the opposite side the accepting gadget will process the information similarly however in Reverse beginning from the base up alright so’s the OSI model.
Yet how might we utilize this to investigate? You may have heard the term or that is a layer 2 issue or seems like a layer 3 issue when you hear that.
That is, individuals alluding to this model suppose there’s an issue with the system on the off chance.
Also Read: Marketing Mix Stimuli
We experience this model checking each layer we can before long analyze the issue for instance layer 1 or the links connected is the system card working would it be able to be a defective link layer 2 perhaps the switch has turned sour layer 3 is the course to working do I have the correct IP address and the procedure continues forever from that point.